Introduction
Deception Technology Solutions for Threat Mitigation have become one of the most effective methods to handle cyber threats in 2025. Every business, from small startups to global enterprises, faces risks from hackers, phishing attempts, ransomware, and insider threats. Traditional firewalls and antivirus tools are no longer enough, because cybercriminals keep upgrading their tactics. This is where deception technology comes in. It creates traps, fake systems, and decoys to confuse attackers, making them waste time while the security team gains critical insights. In this article, we will explore how deception solutions work, their benefits, real-world applications, and why companies across industries are adopting them. To dive deeper into related topics, you can also explore our cybersecurity resources.

What is Deception Technology?
Deception technology is a cybersecurity approach designed to mislead and detect attackers by using decoys, traps, and fake assets across a network. Instead of only blocking threats, this technology sets up a false environment where attackers are drawn in. Once they interact with the decoys, security teams receive alerts in real time.
Key elements include:
- Decoy servers and applications: Fake but realistic versions of company systems.
- Honeytokens and fake data: Files or credentials placed to detect intruders.
- Lures for attackers: Information designed to look valuable but is only a trap.
The main goal is not only to stop attackers but also to study their behavior, identify weak points, and strengthen defenses.
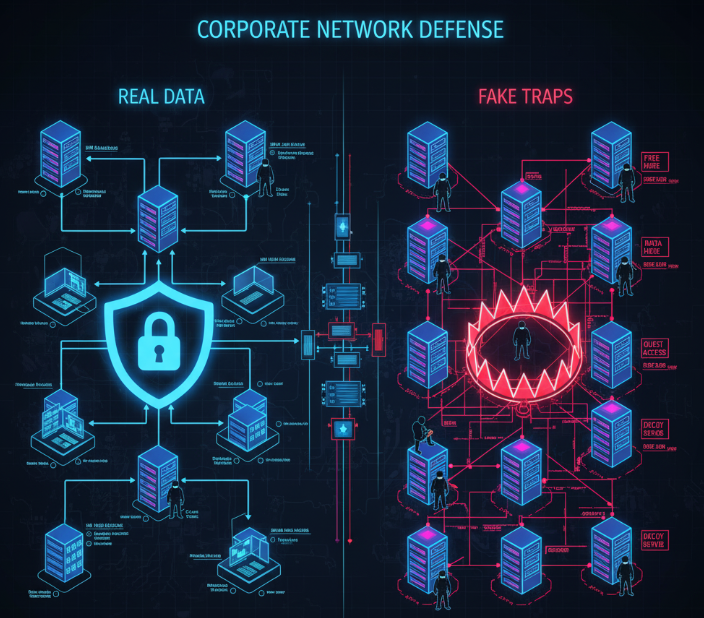
Why Businesses Need Deception Technology Solutions for Threat Mitigation
Today’s cyber threats are more advanced than ever. Attackers use AI-driven malware, phishing campaigns, and zero-day exploits. Even well-protected organizations can fall victim. Deception technology provides a smarter defense because it gives attackers false paths to follow, wasting their resources and reducing risk to actual systems.
Benefits include:
- Early detection: Identifies threats before they reach sensitive systems.
- Low false positives: Because only attackers interact with decoys, alerts are accurate.
- Threat analysis: Helps organizations learn the attacker’s tactics and methods.
- Cost-effective defense: Reduces downtime and prevents financial loss.
- Insider threat detection: Catches malicious insiders trying to access fake assets.
Core Features of Deception Technology Solutions
Deception technology solutions come with a set of features that make them stand out compared to traditional security tools. These features are designed to create a realistic digital environment where attackers cannot easily distinguish between genuine systems and traps.
1. Decoy Systems
Organizations can set up fake servers, databases, and applications that appear to hold valuable information. When attackers attempt to interact with them, alerts are instantly triggered.
2. Honeytokens and Fake Credentials
These are small pieces of false data such as login details, documents, or API keys. When attackers use them, security teams know immediately that someone unauthorized is inside the system.
3. Advanced Monitoring & Alerting
Deception technology integrates with SIEM (Security Information and Event Management) tools, so any suspicious activity from decoys is reported without delay.
4. Threat Intelligence Gathering
Unlike basic security solutions, deception tools collect detailed information about the attack methods, malware types, and strategies hackers use.
5. Easy Deployment
Most modern solutions are designed to be scalable and can be deployed across cloud, hybrid, or on-premises environments with minimal disruption.
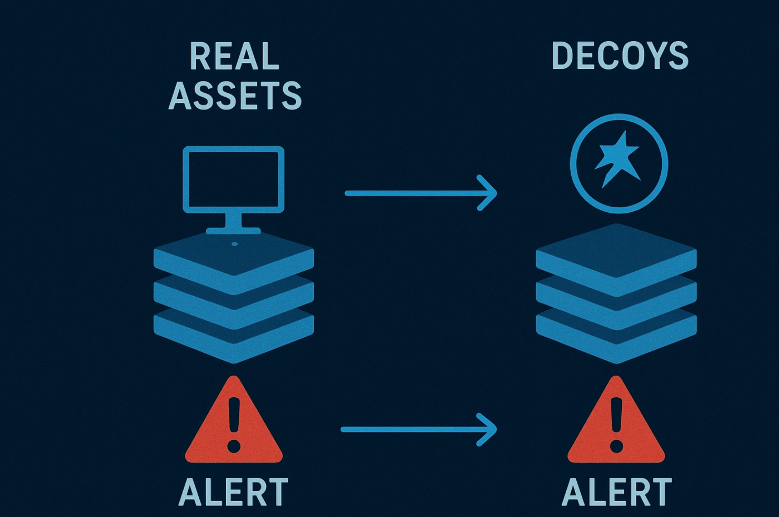
Real-World Applications of Deception Technology
Deception technology is not limited to a single industry. Its flexibility makes it useful in multiple sectors where cybersecurity is crucial.
- Banking and Finance: Protects customer data, payment systems, and online transactions from cyber fraud.
- Healthcare: Secures patient data and prevents ransomware attacks on hospitals.
- Government Agencies: Defends against nation-state threats and espionage.
- Retail & E-commerce: Protects payment gateways and customer records.
- Education: Safeguards research data and prevents breaches in digital learning platforms.
- Telecommunications: Secures large-scale networks from external and insider attacks.
Pros and Cons of Deception Technology Solutions for Threat Mitigation
Pros:
- Early detection of attacks.
- Minimal false positives compared to traditional firewalls.
- Works well with existing cybersecurity tools.
- Provides insight into attacker behavior.
- Effective against insider threats.
Cons:
- Requires skilled IT teams to manage.
- Can be complex to integrate in very large networks.
- Not a complete replacement for traditional defenses — must be combined with firewalls, antivirus, and monitoring tools.
Case Studies: How Organizations Use Deception Technology
To better understand the impact of deception technology, let’s look at a few real-world scenarios where it has been successfully applied.
1. Financial Sector
A global bank deployed deception systems across its digital branches. Fake transaction records and decoy login portals were placed to track attackers. Within months, the bank was able to detect multiple intrusion attempts that traditional firewalls failed to catch.
2. Healthcare Industry
A hospital network faced constant ransomware attacks. By using deception traps such as fake patient records and decoy servers, they identified hackers before real patient data was touched. This protected both their reputation and compliance with regulations.
3. Government Agencies
Several agencies use deception solutions to defend against state-sponsored attacks. Fake communication channels and decoy classified files help detect espionage attempts early.
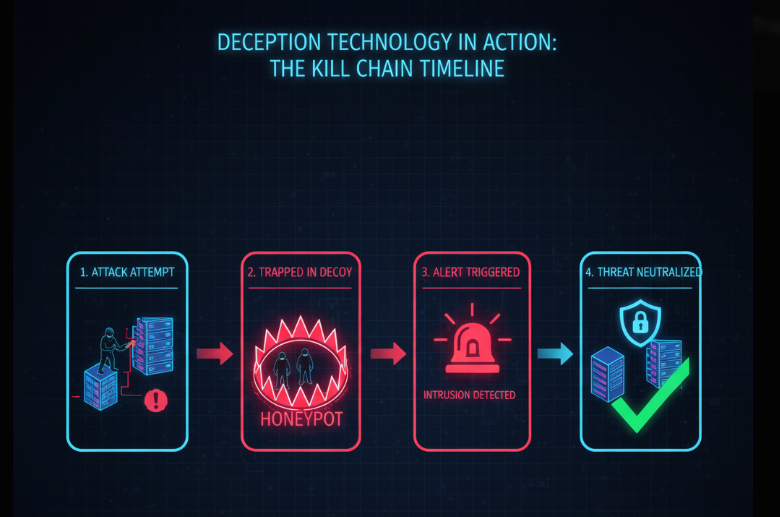
Future Trends in Deception Technology (2025 and Beyond)
The cybersecurity world is changing rapidly, and deception technology is evolving with it. In 2025, organizations can expect:
- AI-Driven Deception: Decoys will adapt in real-time using machine learning.
- Integration with Zero Trust Models: Ensures no user or system is trusted by default.
- Cloud-Native Deception: Designed for hybrid and multi-cloud environments.
- Automation and Orchestration: Reduced human effort as AI handles detection.
- Increased Adoption: More small businesses will begin using deception due to affordable solutions.
Best Practices for Implementing Deception Technology
Organizations looking to adopt deception solutions should keep in mind the following practices:
- Start Small: Begin with a pilot program before full deployment.
- Integrate with Existing Tools: Deception works best with SIEM, firewalls, and antivirus.
- Train Security Teams: Ensure staff can analyze alerts and act quickly.
- Focus on High-Value Assets: Place decoys around critical databases and systems first.
Review and Update Regularly: Attack strategies change, so deception systems must evolve too.
Comparison Table: Traditional Security vs. Deception Technology
| Feature | Traditional Security | Deception Technology |
|---|---|---|
| Detection Speed | Slow, often after damage | Fast, real-time alerts |
| False Positives | High | Low (only attackers trigger traps) |
| Insider Threat Protection | Weak | Strong, traps insider access |
| Cost Efficiency | High long-term cost | Cost-saving by preventing damage |
| Threat Analysis | Limited insights | Detailed attacker behavior study |
Graph: Industry Adoption of Deception Technology
Conclusion
Deception Technology Solutions for Threat Mitigation are no longer optional — they are becoming essential in modern cybersecurity. By creating traps, decoys, and false paths for attackers, these solutions protect valuable data while also providing intelligence about how hackers operate. Businesses that adopt deception technology gain a strong advantage, reducing the risk of data breaches and financial loss.
Whether in banking, healthcare, or government sectors, deception is proving to be a reliable and future-ready defense. As cyber threats grow smarter in 2025, organizations that use deception technology will be one step ahead of attackers.