In recent years, the rise of Quantum-Resistant Encryption has become a major topic in cybersecurity. Traditional encryption methods like RSA and ECC have been considered secure for decades, but the development of quantum computers threatens to break them within seconds. This reality pushes organizations, researchers, and even governments to adopt new encryption standards that can withstand the power of quantum computing. In this guide, I will explain what quantum-resistant encryption is, why it matters in 2025, how it works, its algorithms, pros and cons, and what industries need it the most.

What is Quantum-Resistant Encryption?
Quantum-resistant encryption, sometimes called post-quantum cryptography, refers to cryptographic algorithms designed to secure data against attacks from quantum computers. Unlike classical systems, quantum machines use qubits, allowing them to perform complex calculations exponentially faster. This capability threatens widely used encryption standards, making sensitive information vulnerable. Quantum-resistant methods aim to create encryption keys and algorithms that even a powerful quantum machine cannot crack.
These solutions are not just theoretical anymore. Global organizations such as NIST (National Institute of Standards and Technology) are already standardizing algorithms that fall under the post-quantum category. By preparing now, businesses ensure that their data remains protected for decades to come.
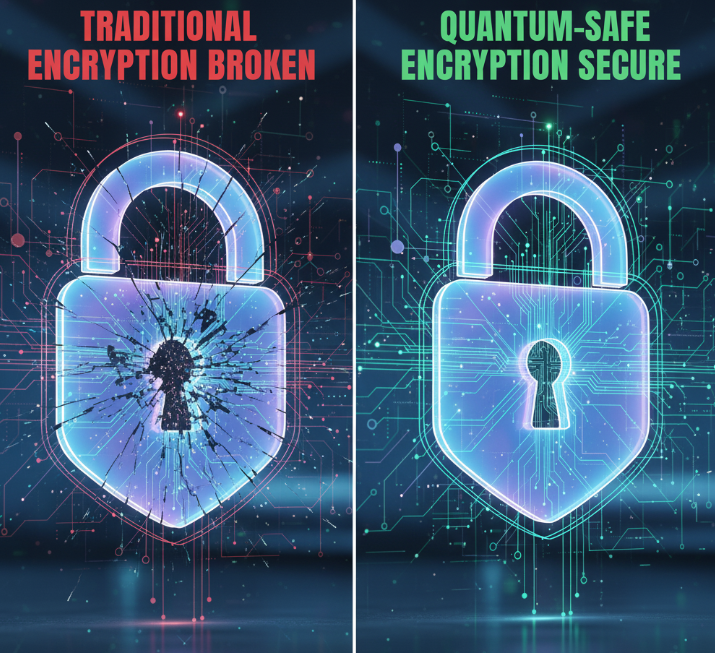
Why Do We Need Quantum-Resistant Encryption?
The urgency for quantum-resistant encryption lies in the fact that once quantum computers reach maturity, they can break existing encryption like RSA-2048 in mere minutes. Today’s hackers can store encrypted data and wait until quantum power is available to decrypt it later. This is known as the “Harvest Now, Decrypt Later” attack.
Key reasons include:
- Protecting sensitive government and defense data.
- Securing healthcare and financial systems.
- Future-proofing enterprise security investments.
- Meeting compliance and regulatory standards.

Core Algorithms Behind Quantum-Resistant Encryption
Quantum-resistant encryption relies on mathematical problems that remain hard even for quantum computers. NIST has shortlisted several algorithms in this category. Some of the popular ones include:
- Lattice-based cryptography – relies on the complexity of lattice problems, widely believed to be quantum-safe.
- Hash-based cryptography – suitable for digital signatures, very secure but sometimes larger in size.
- Multivariate quadratic equations – encryption using complex polynomial equations.
- Code-based cryptography – known since the 1970s, still unbroken by quantum methods.
These algorithms are being standardized and will soon replace today’s RSA and ECC in practical applications.
Real-World Use Cases
Quantum-resistant encryption isn’t limited to theoretical labs. It’s already being tested in different industries:
- Banking & Finance: Protecting transactions and customer data.
- Healthcare: Securing patient records and drug research data.
- Government & Military: Ensuring classified communication remains private.
- Cloud Providers: Future-proofing cloud storage and SaaS platforms.
- IoT Devices: Small but critical devices that need lightweight encryption.

Benefits of Quantum-Resistant Encryption
- Future-proof security against both classical and quantum attacks.
- Protection of long-term sensitive data.
- Compliance with upcoming international regulations.
- Higher trust in industries like banking and healthcare.
- Ensures innovation in AI and blockchain without risk of exposure.

Challenges and Limitations
While promising, these solutions are not without challenges:
- Larger key sizes compared to RSA.
- Higher computational demand.
- Slower adoption due to lack of awareness.
- Compatibility issues with existing systems.
- Cost of implementation in large-scale enterprises.

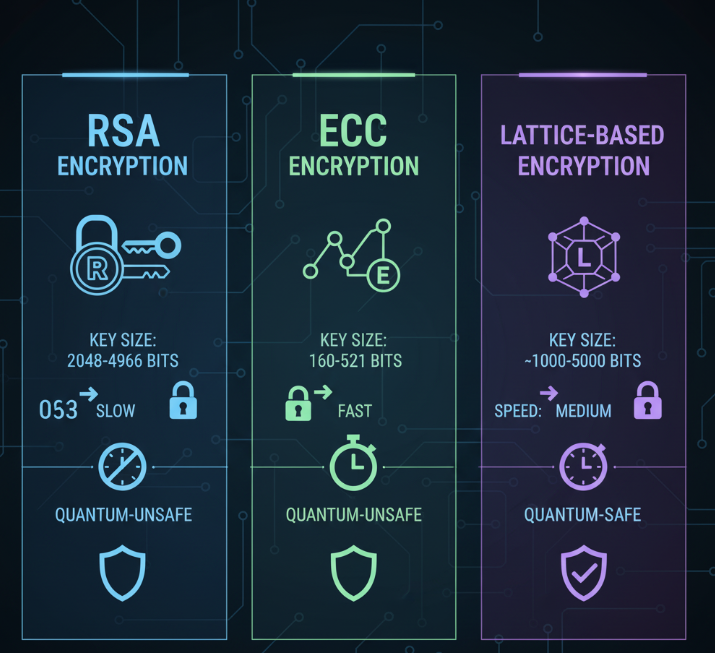
Comparison Table
Here’s a quick comparison of traditional vs quantum-resistant algorithms:
| Encryption Type | Strength | Quantum Resistance | Use Case |
|---|---|---|---|
| RSA-2048 | Strong (today) | Not resistant | Banking, websites |
| ECC | Strong (today) | Not resistant | Mobile devices |
| Lattice-based | Very strong | Quantum resistant | Future standards |
| Hash-based | Strong | Quantum resistant | Digital signatures |
| Code-based | Strong | Quantum resistant | Legacy secure systems |
Graph: Rising Adoption of Quantum-Resistant Encryption (2020–2030)
Final Thoughts
Quantum-resistant encryption is no longer a distant future topic. With rapid progress in quantum computing, traditional cryptography faces real threats. By adopting quantum-resistant solutions early, businesses can secure their data, comply with regulations, and maintain trust in the digital age. Just like the transition from HTTP to HTTPS became a global standard, quantum-safe encryption will soon become a baseline requirement for every organization, setting the new standard for future encryption methods.